I found an article recently that showed the use of QuickHash to check password strings and then using the resulting hash in one of the many sites that store hashes of passwords from data breaches. I then also found this article by The Register titled 'Crypto-busters reverse nearly 320 MEELLION hashed passwords' that talks about the same thing in a lot more detail : https://www.theregister.co.uk/2017/09/04/cryptobusters_reverse_nearly_320_meellion_hashed_passwords/
You can read more about Troys work and the concept of password hashes and their availability here : https://www.troyhunt.com/introducing-306-million-freely-downloadable-pwned-passwords where he continues to talk about using the SHA-1 hash of a password to check the pawned directory and to see if that is in the list:
"To give people more options, they can also search for a SHA1 hash of the password. Taking the password "p@55w0rd" example from earlier on, a search for "ce0b2b771f7d468c0141918daea704e0e5ad45db" (the hash itself is not case sensitive so "CE0B…" is fine too) yields the same result"
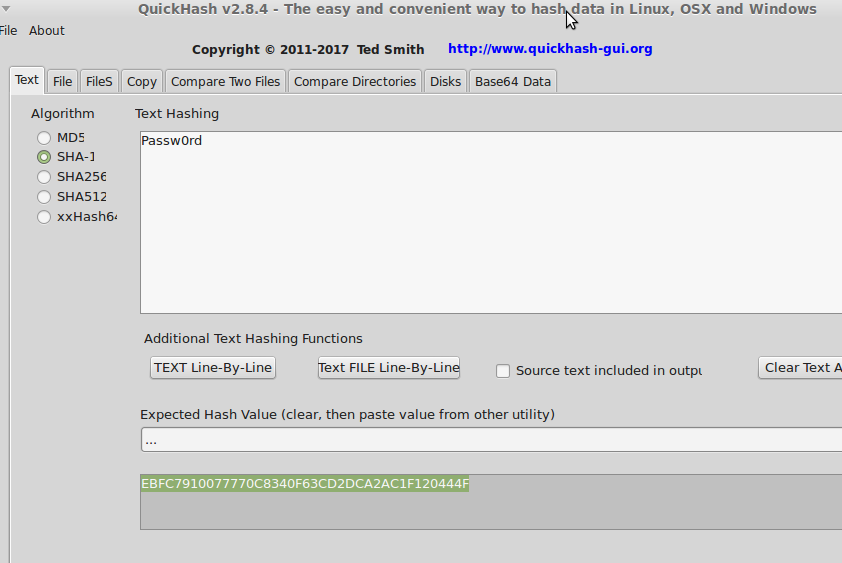
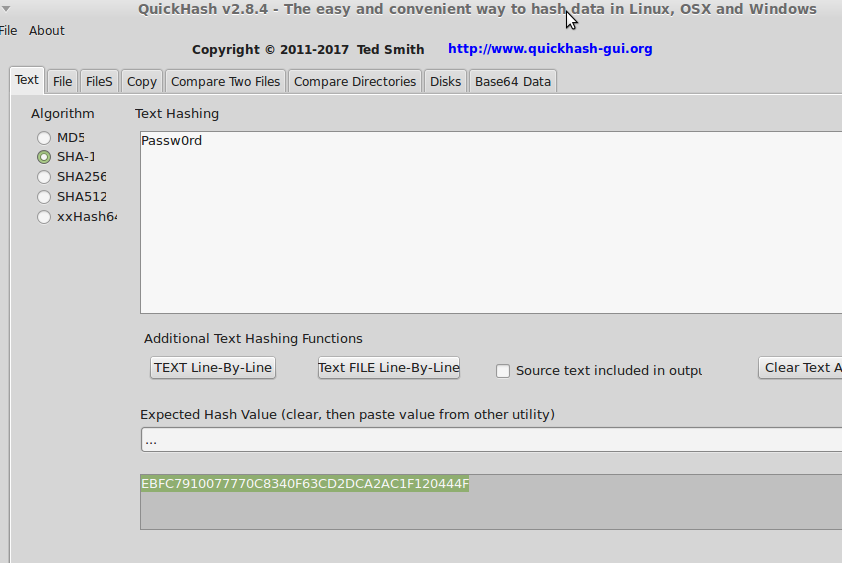
So for examples, 'Passw0rd' has the SHA-1 hash EBFC7910077770C8340F63CD2DCA2AC1F120444F (as you can see by the Linux version of QuickHash screenshot below), so when I paste that into https://haveibeenpwned.com/Passwords
it tells me immediately that it has been used somewhere and has been hoovered up in a data breach. So you can use the program to easily generate SHA-1 hashes of your passwords and test them on such sites without having to pass an actual password, or at least certainly not one you are thiking of using as a new password (which even HaveIBeenPwned don't advise).



I just went through this in 2022 and quickhash-gui does not have the required functions.
Since the originally suggested site is down, google for “sha512 / crypt(3) / $6$ generator” and you will find online generators that support that salted hash.
I am not sure how I missed these two comments – sorry! But you are both correct – QuickHash-GUI does not currently support the salted hash issue.
Will this help me created a new salted hash to solve login problems with ubiquity unifi manager?
The online tool for crypt3-sha512-online is existentially challenged :(
People will find this while looking for 9Ter1EZ9$lSt6 (if the tool cannot best to remove this third comment line)